Empower ID Overview
Empower ID is an all-in-one, converged platform that was developed as a comprehensive solution for identity management and access governance. It serves as a robust tool for organizations looking to streamline processes related to identity and access, ensuring that every component of identity management—from creation to access rights—is housed within a single platform. This eliminates the need for multiple disparate systems, promoting efficiency and coherence in identity and access management.
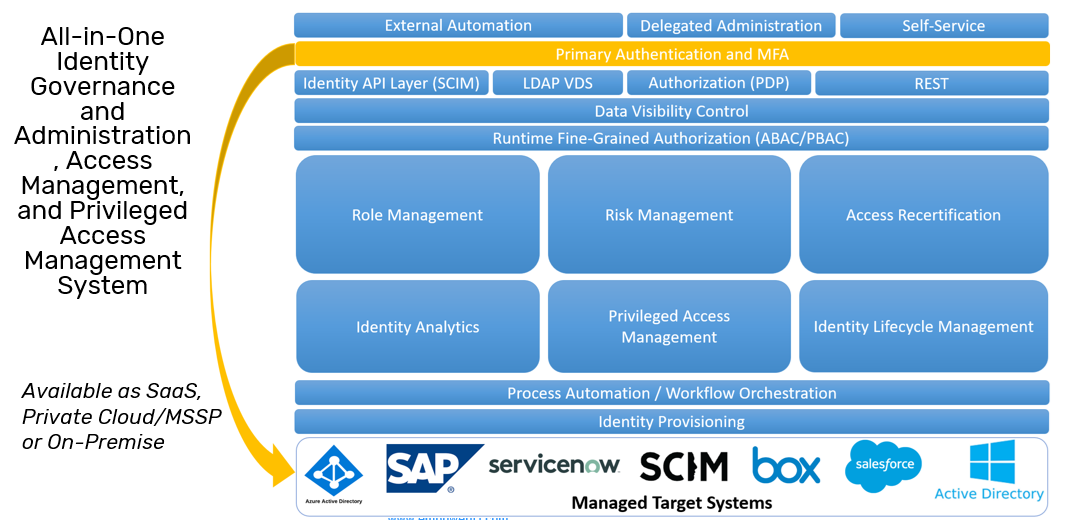
Key Features of EmpowerID
-
Identity and Access Management (IAM): At the heart of Empower ID is its ability to manage digital identities effectively. This includes creating, provisioning, and synchronizing identities across various systems within an organization. Empower ID allows clients to connect seamlessly with a wide range of target systems, making it easier to manage user identities no matter where they reside.
-
Identity Warehouse: Unlike traditional directory systems (such as Active Directory or LDAP) that operate on a singular identity store, Empower ID functions as an identity and entitlement warehouse. This model allows it to manage and pull information from various sources (like Azure Active Directory, SAP, ServiceNow, etc.) into one aggregated identity warehouse, thus providing visibility and manageability across multiple directories and landscapes.
-
Process Automation and Workflow Orchestration: Empower ID goes beyond identity provisioning by offering rich process automation capabilities. The platform enables workflow orchestration to manage how identity information is processed and manipulated across the various management processes it supports.
-
Core Functionality: Empower ID integrates features such as identity analytics, privileged access management, identity lifecycle management, access recertification, and risk management into its core framework. These features are aimed at ensuring that the management of identities is aligned with the security needs of the enterprise, helping to mitigate risks associated with unauthorized access.
-
Security Infrastructure: To protect the privacy and integrity of identity processes, Empower ID incorporates advanced security frameworks, including role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control (PBAC). This facilitates fine-grained authorization which is crucial for maintaining a secure identity management architecture.
-
Communication and Integration Capabilities: The platform features a comprehensive Identity API layer, enabling integrated communication with external systems through various protocols such as REST APIs, LDAP services, and others. This module ensures that Empower ID can interact effectively with all other enterprise systems.
-
End User Interaction: End users experience the capabilities of Empower ID through features such as Primary Authentication and Multi-Factor Authentication (MFA). These are crucial for safeguarding access to sensitive resources, ensuring that user identities are verified adequately before granting access.
In essence, Empower ID serves as a holistic solution, combining identity provisioning, access management, and workflow automation into an integrated platform tailored to meet the needs of modern organizations. This comprehensive architecture is designed to facilitate seamless management and governance of identities across varying environments, thereby reducing complexity and enhancing security measures across organizational structures.
The Identity and Entitlement Warehouse
At its core, Empower ID operates as an identity and entitlement warehouse, which is sometimes referred to as a meta-directory. However, it is more accurately described as an entitlement and identity warehouse, which provides a robust framework for managing identities and permissions across multiple systems and directories.
Key Aspects of the Identity and Entitlement Warehouse:
Distinction from Traditional Directory Services
Unlike traditional directory services such as Azure Active Directory, LDAP, or Novell E-Directory, which maintain a single identity store specific to a particular system, the identity warehouse of Empower ID aggregates all identity and entitlement data from a diverse range of systems. This allows it to manage and pull together information from multiple sources, providing a consolidated view of identities across the enterprise landscape.

Capabilities of the Identity Warehouse:
-
Connection to Multiple Directories: Empower ID can integrate with an extensive array of directory services and external systems, such as SAP, Azure Active Directory, ServiceNow, Workday, and more. This capability allows the platform to inventory and ingest information from these various directories into its identity warehouse.
-
Visibility and Manageability: The warehouse facilitates visibility into and management of all identities within the organization. This is particularly beneficial for managing users who may have accounts across multiple systems, as it empowers administrators with an overview of entitlements associated with each identity.
-
Password Synchronization: One of the significant advantages of the identity warehouse is its ability to synchronize passwords across multiple systems. For instance, when a user resets their password, this change can be propagated throughout various managed systems (e.g., IBM, SAP, Microsoft, Salesforce), ensuring consistency and enhancing security.
-
Delegated Identity Administration: The identity warehouse supports centralized delegated management of identity administration processes across various platforms, allowing for a least-privilege approach to delegated administration.
-
Risk Management and Segregation of Duties: The identity warehouse's structure is conducive to managing risk and enforcing segregation of duties (SoD) policies. Administrators can define and evaluate policies that prevent conflicts (e.g., ensuring that a role in an SAP system does not have corresponding access in Active Directory) across multiple directories. This capability is crucial for compliance and governance.
-
Access Recertification: Administrators can perform access recertification procedures across all managed systems simultaneously, enhancing overall management of identity entitlements.
-
Master Identity Management: Empower ID allows for the joining of various accounts (e.g., SAP account, Azure AD account, ServiceNow account) to a master identity, referred to as a person identity within Empower ID. This feature creates a unified view of all identities associated with an individual, allowing for streamlined identity management and attribute synchronization across disparate systems.
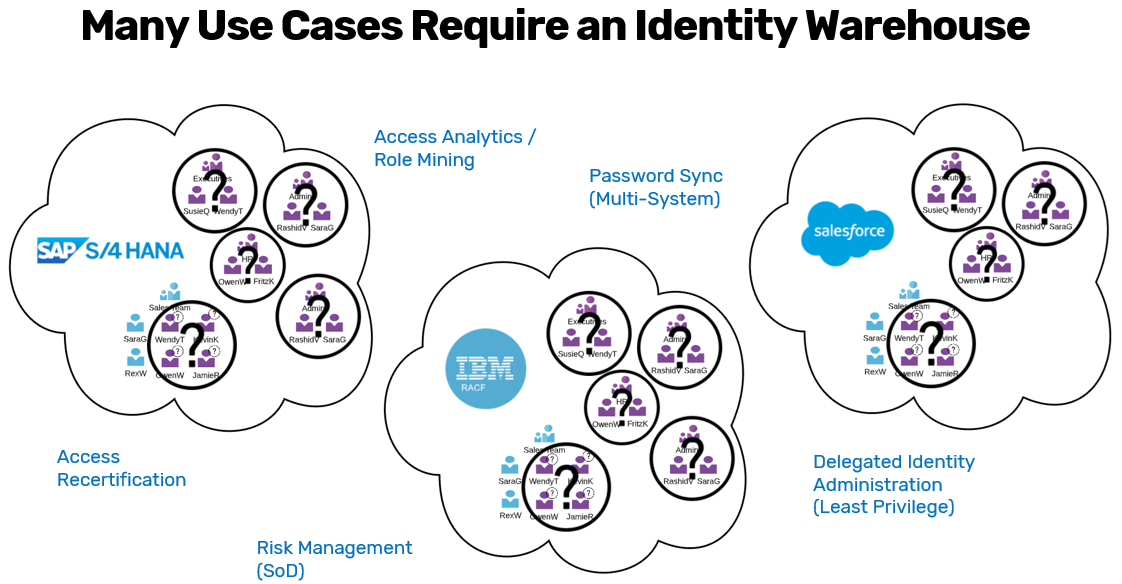
Structure of the Identity Warehouse
The underlying architecture of the identity warehouse is built upon a robust SQL database, specifically the Microsoft SQL Server. This database houses a comprehensive collection of data, including:
- Over 1,200 tables
- Approximately 700 views
- More than 20,000 stored procedures or method calls
This complex structure allows for efficient data management and processing.
Interaction with Identity Objects
Within the Empower ID framework, each object stored in the identity warehouse is represented as a component. Each component has its own properties, attributes, and stored procedures, allowing for a high degree of automation and customization in identity management workflows. For instance, when dealing with account objects, a wealth of attributes and metadata is associated with those components to enable better resource management.
In summary, the identity and entitlement warehouse serves as the backbone of the Empower ID platform, enabling organizations to manage identities and their associated entitlements effectively. Its architectural design, robust integration capabilities, and emphasis on risk management and administration ensure that organizations can meet their identity governance and compliance requirements while enhancing operational efficiency.
Identity Model
The Identity Model within Empower ID is critical for understanding how the platform manages various identity types and their relationships to one another. This section defines the primary identity types, their roles, and the relationships among them within the Empower ID framework.
Key Identity Types
-
Person Identity
- The person identity is the central managed identity within Empower ID. It represents a distinct and separate identity for individuals within the organization.
- Think of the person identity as the "user" in Empower ID. It serves as the primary aggregating component for all accounts that a particular person owns across different systems.
- Roles and access assignments (such as role-based access control/RBAC, attribute-based access control/ABAC) are all derived from this managed identity, which is essential for defining access privileges and permissions across the platform.
-
Accounts
- Accounts represent technology-based identities associated with external systems. Each person identity can have multiple accounts corresponding to different systems—like Active Directory accounts, SAP accounts, or LDAP accounts.
- These accounts are linked to the person identity to establish ownership and relationships, allowing for a comprehensive view of what resources a person can access and within which systems.
-
Core Identity
- The core identity serves as a unique representation of an individual or entity within the enterprise. It acts as the overarching link between multiple managed identities.
- This concept enables organizations to manage cascading events—such as terminations or role changes—effectively. For example, if an employee’s primary identity needs to be deactivated due to termination, actions can cascade to any related managed identities.
Relationships Among Identity Types
The relationships among these identity types are significant for effective identity management:
-
Aggregation and Management: The core identity provides a vehicle through which you can track various managed identities that belong to a single individual. In practice, for someone like "Joe Smith," who may have a standard operational identity (managed identity) and an administrative identity (separate managed identity), both can be connected through one core identity.
-
Cascading Operations: If there’s a need to perform actions such as terminations or updates, the cascading nature allows for systematic deactivation or modification of associated accounts based on the primary person identity’s status.
-
Example Scenario:
- Joe Smith has a primary managed identity, say "Joe_123," connected to various accounts such as his HR identity, Microsoft Active Directory account, and other system accounts.
- Simultaneously, he may also possess an additional managed identity like "Admin_Joe," with separate privileges and accounts linked to admin roles or support tasks.
- Here, the core identity serves to connect "Joe_123" and "Admin_Joe," ensuring that when an operation affecting Joe Smith must be executed (like termination), all associated identities are updated accordingly without the risk of missing a secondary identity.
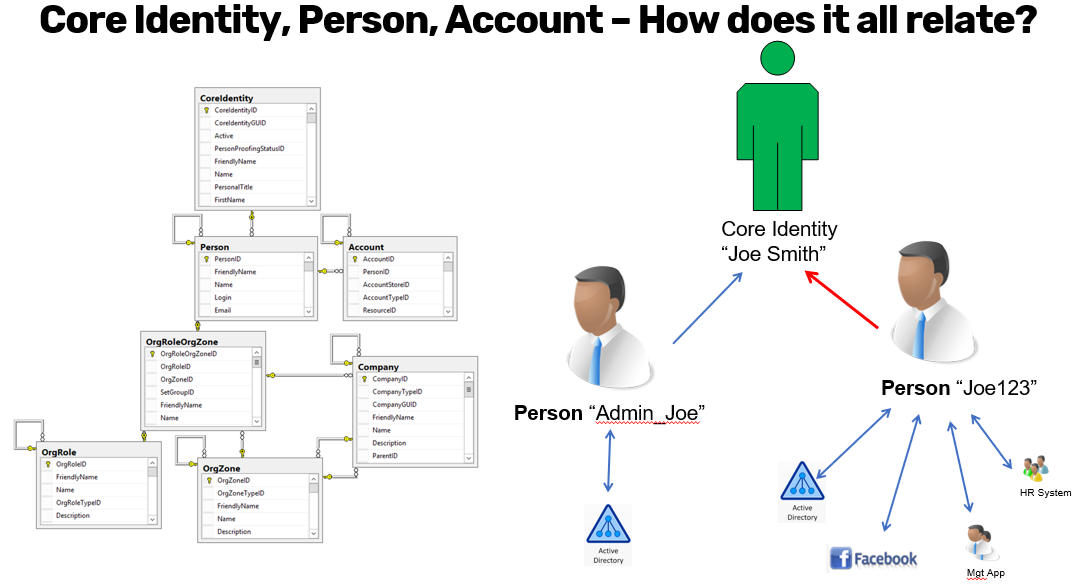
When to Use Person Objects
Certain conditions necessitate the creation of a person object for an account:
- If the account will be utilized for logins, such as in applications or REST APIs.
- If there’s a need for managing access via an identity management system (e.g., an IAM shop).
- If policies related to access roles need to be assigned to that account.
- To separate and manage attribute changes to ensure no cross-contamination of data between distinct accounts (e.g., standard user account vs. admin account).
The Role of Core Identities
Core identities play a crucial role when managing multiple person identities. The following scenarios merit the use of core identities:
- If several accounts within the same directory need to be managed under one umbrella (i.e., Core Identity).
- When an individual has privileged access that needs to be segregated from day-to-day access.
- In the management of synchronized attribute values for accounts associated with one person identity.
Summary Key Takeaways
- The person identity in Empower ID is the managed user object in the system, and it aggregates various accounts owned by an individual.
- Not all accounts require a dedicated person object—service accounts may be managed as standard accounts.
- Person objects must be created whenever HR records are involved to align identities with organizational data.
- The core identity is ultimately optional but is beneficial in complex scenarios where multiple identities must be managed coherently.
By delineating these identity types and their interrelationships, organizations can better navigate the complexities of identity management and utilize Empower ID to its fullest potential.
Authentication in Empower ID
Authentication is a critical component of the Empower ID platform, ensuring that only authorized users can access the system and its resources. Empower ID offers multiple methods for authentication, facilitating flexibility while adhering to security best practices.
Key Aspects of Authentication in Empower ID
Multiple Authentication Methods
Empower ID supports various identity providers (IdPs) for user authentication, including:
- Azure Native Authentication
- Active Directory
- ADFS (Active Directory Federation Services)
- Social Media Logins (e.g., Facebook, Google)
- Other SAML or OIDC-compliant Providers
This flexibility is crucial as it allows organizations to leverage existing identity providers while maintaining a consistent user experience across platforms.
Authentication Process
The authentication process within Empower ID follows a systematic approach:
-
User Selection of Identity Provider:
- When users attempt to log in to Empower ID, they choose their identity provider from a list presented on the login page.
-
Credential Input:
- Users enter their credentials (username/password) for the selected identity provider.
-
Validation against IdP:
- The provided credentials are sent to the selected identity provider for validation. This could involve checking against a directory like Azure Active Directory or an external federated identity system.
-
Empower ID Verification:
- Upon successful validation, Empower ID retrieves the user’s identity information from the IdP and checks if the authenticated account is linked to a corresponding managed person identity within Empower ID.
-
Completion of Login:
- If the account is successfully joined to a managed person identity, the user gains access to the Empower ID platform. If it is not linked, the authentication process fails, preventing access.
-
Role Assignments:
- As part of the authentication process, role assignments can also be evaluated, determining what resources and permissions the user has access to based on their person identity.
Multi-Factor Authentication (MFA)
Empower ID also incorporates Multi-Factor Authentication (MFA) as an additional security layer to enhance identity verification. MFA requires users to provide two or more verification factors to gain access to a resource, making it significantly harder for unauthorized users to gain entry. Common MFA methods include:
- SMS or email codes
- Authentication apps (like Google Authenticator)
- Biometric verification (fingerprint, facial recognition)
The inclusion of MFA helps organizations comply with security policies and regulations, reinforcing the principle of least privilege by ensuring that accessing sensitive resources requires robust authentication.
End User Experience
The user interface for logging into Empower ID is streamlined to support a seamless authentication experience. Users can easily navigate through the available identity providers, complete their logins with minimal friction, and access applications conveniently, thanks to SSO functionality.
Key Considerations for Authentication
- Integration with Existing Systems: Organizations need to carefully plan how Empower ID's authentication mechanisms integrate with existing identity providers to ensure a smooth transition and maintain user experience.
- Security Policies: Organizations should define clear security policies around password management, MFA usage, and access privileges related to authentication to enhance overall security posture.
- Monitoring and Reporting: Regular monitoring of login attempts and the authentication processes is essential for detecting any unauthorized access attempts and ensuring compliance with auditing requirements.
In summary, authentication within Empower ID is designed to be flexible, secure, and user-friendly. By supporting multiple identity providers, SSO, and MFA, Empower ID enables organizations to effectively manage access while safeguarding sensitive resources from unauthorized users. Understanding the authentication process and its components is fundamental for leveraging Empower ID's capabilities in identity and access management.
Workflow Model
The workflow model within Empower ID is a powerful aspect of the platform that enables automation and orchestration of identity and access management processes. Empower ID utilizes two main types of workflows—low code and no code—to facilitate these functionalities, allowing organizations to adapt workflows according to their specific operational needs.
Key Components of the Workflow Model
Low Code Workflows
Low code workflows in Empower ID consist of executable processes that can be maintained and managed through the Workflow Studio. Designed for flexibility, these workflows require minimal coding knowledge, enabling users to create and modify workflows based on business requirements easily.
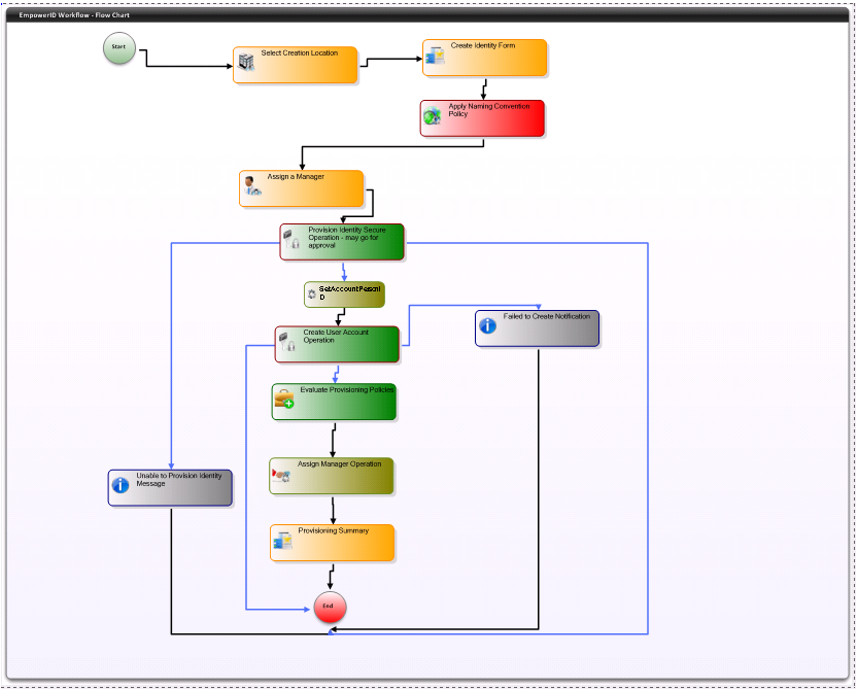
How Low Code Workflows Operate:
-
Execution of Workflow Processes: Each low code workflow is treated as a single executable process. Users can initiate workflows by clicking on options (e.g., “Create Person and Account”).
-
Series of Activities: When a workflow is initiated, various predefined activities are executed sequentially. These activities can include creating new identities, updating permissions, or modifying access rights.
-
Authorization Mechanism: For certain operations—especially those that impact or manipulate protected resources—Empower ID implements an authorization process. If a user attempts to execute an operation that requires permissions beyond their current access level, the system will evaluate their authorizations.
-
Approval Process: If the user lacks the necessary permissions, the workflow is paused, and the appropriate approval process is initiated. This ensures that actions affecting sensitive resources are controlled and documented, maintaining compliance and security.
-
User Interface Elements: Low code workflows are integrated with user interface (UI) elements that allow users to interact with the system seamlessly. The UI elements present options to users clearly while enforcing security checks through the underlying RBAC and other authorization measures.
-
Auditing and Reporting: Every workflow execution, including its initiation, changes, and approvals, is logged. This audit trail provides organizations with the essential data necessary for compliance monitoring, internal reviews, and investigation of discrepancies.
Benefits of the Workflow Model
-
Increased Efficiency: By automating routine identity management tasks, the workflow model reduces manual intervention, speeding up processes and reducing the likelihood of human error.
-
Enhanced Flexibility: The low code and no code capabilities of the workflow model allow organizations to quickly adapt to changing business needs or regulatory requirements by easily modifying existing workflows or creating new ones.
-
Improved User Experience: Users benefit from clear interfaces that guide them through processes, along with streamlined authorization steps that keep operations running smoothly.
Summary
The workflow model within Empower ID is an integral part of the platform that provides the necessary tools for automating and managing identity and access management processes. With its low code and no code workflows, organizations can streamline operations while enforcing security measures to protect sensitive resources effectively. By understanding the intricacies of the workflow model, users can leverage Empower ID to its fullest potential, improving efficiency and compliance within their identity management systems.
Connector Topology
Empower ID features a versatile connector topology that is key to its ability to integrate with various external systems and directory services. This model enables seamless interaction between the Empower ID platform and the resources it manages, laying the groundwork for streamlined identity and access management across diverse environments.
Types of Connectors
Empower ID provides four primary types of connectors, each designed for specific integration scenarios:
-
Stock Connectors
- Stock connectors come pre-packaged with Empower ID and are designed to offer robust identity management capabilities for commonly used systems.
- Examples of supported systems include:
- Azure Active Directory
- Salesforce
- SAP SuccessFactors
- LDAP
- Microsoft Exchange
- These connectors facilitate straightforward integration with target systems, enabling capabilities such as identity provisioning, synchronization, and management with a minimal configuration overhead.
-
Universal Connectors
-
The universal connectors are flexible options that cater to systems for which stock connectors are not available.
-
They come in two forms:
- Flat File Universal Connector: Allows the ingestion of data from flat files, making it easier to integrate with legacy systems or other data sources that output CSV or similar formats.
- Database-Based Universal Connector: This option utilizes an intermediary universal connector database where customers can write their data into well-defined and documented schema which is then processed into EmpowerID through standard UI-based account store definition processes.
-
Both types of universal connectors can be configured through the Empower ID user interface, combined with basic workflow processes, ensuring that organizations can connect to most systems without extensive coding requirements.
-
-
Custom Connectors
- Custom connectors are built to address specialized use cases where neither stock nor universal connectors suffice.
- Organizations can create these connectors to meet specific integration needs or complex scenarios requiring tailored workflows.
- Custom connectors can be developed through two main approaches:
- Code-Based Libraries: Utilizing the Workflow Studio to write custom code that interacts with an external system.
- CRUD Service Connectors: Leveraging Empower ID's new CRUD service framework to create connectors without needing deep SKIM (System for Cross-domain Identity Management) or Empower ID knowledge.
-
SCIM Microservice Framework Connectors
- These connectors are designed in accordance with the SCIM 2.0 standards, which simplify the process of developing integrations for different platforms.
- They can be easily developed without extensive knowledge of either Empower ID or SCIM protocols, providing a user-friendly option for creating compliant connectors.
- The SCIM microservice framework enables smooth management of identities across platforms, facilitating multi-tenant configurations as needed.
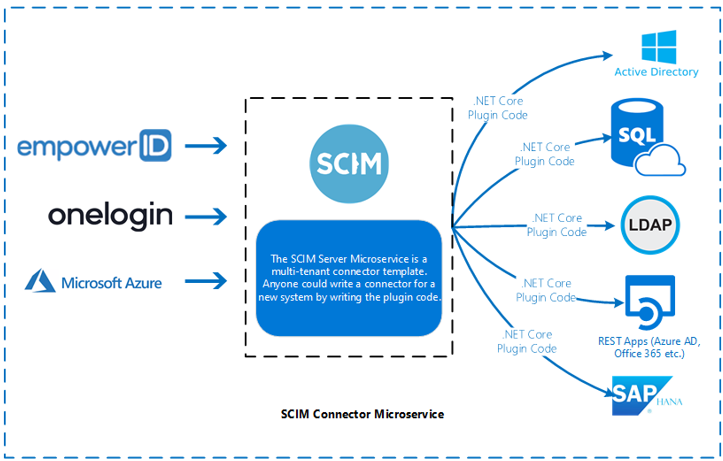
Depth of Connector Functionality
Some connectors offer in-depth functionality that goes beyond basic identity management:
- Azure Connector: This connector allows not only for the management of Azure users and groups but also delves into specific Azure resources, such as service principals, managed identities, Admin Roles, RBAC Roles and Azure subscriptions. This ensures that organizations can effectively manage their cloud resources in conjunction with on-premises systems.
- SAP Connector: The SAP connector can handle a comprehensive view of SAP environments, managing roles, transaction codes (T-codes), and relationships among these elements to maintain a secure SAP landscape.
Connector Configuration and Management
Empower ID's connectors can be easily configured and managed through its interface. The setup process allows administrators to define the scope of connected systems, set synchronization schedules, and configure how data will flow between Empower ID and external systems.
-
Integration with Existing IT Systems: These connectors facilitate the integration of Empower ID with existing IT systems and applications, ensuring organizations can consolidate identity management without needing to replace their current infrastructure.
-
Real-Time Synchronization: All of the connectors support flexible and configurable scheduled synchronization of identity data with external systems, helping maintain updated and accurate records across platforms.
-
Support for Diverse Protocols: Empower ID connectors leverage a range of protocols, including REST APIs, SCIM, LDAP, and others, allowing for broad compatibility with varying external systems.
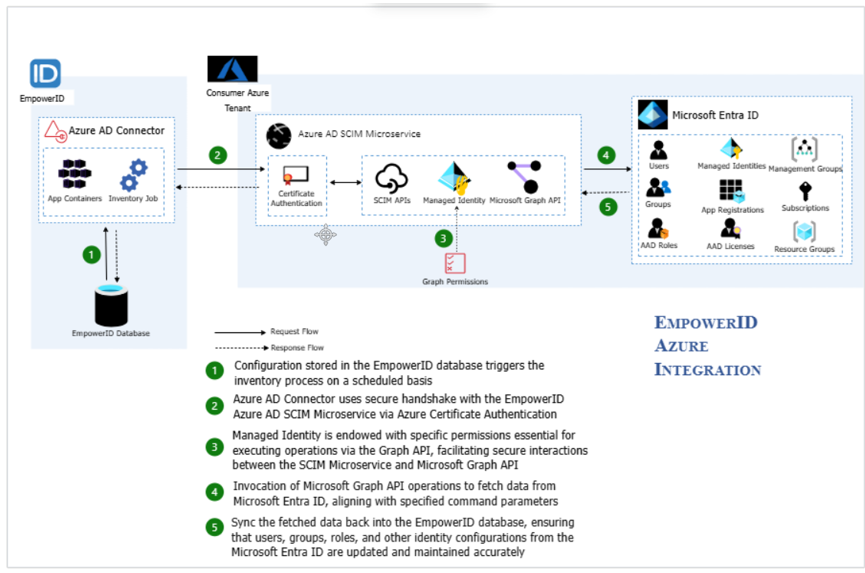
Understanding the EmpowerID Cloud Gateway
The EmpowerID Cloud Gateway is a crucial component that enables secure communication between your on-premises systems and the EmpowerID Cloud. It is a small, lightweight Windows application that acts as a connectivity gateway between the customer environment and the EmpowerID SaaS tenant. It enables the EmpowerID Cloud SaaS tenant to inventory and manage on-premise systems without requiring ports to be opened on their firewall. The Cloud Gateway is a lightweight application that users can install on a Windows 10 desktop or server inside the on-premise network. Upon installation, the Cloud Gateway generates a public and private PKI certificate and registers the public key in the customer’s SaaS tenant for encrypted and secure communications. The Cloud Gateway then makes a secure and encrypted outbound HTTPS (TLS) connection to an EmpowerID queue in Azure as a bridge for communication between the EmpowerID Cloud servers and the customer’s on-premise network. Customers may install multiple Cloud Gateways on-premise for fault tolerance and increased performance.
How the Cloud Gateway Works:
Before installing the Cloud Gateway Client (CGC) on a server, you need to create an EmpowerID Person with access to register and ping a Cloud Gateway server. You then use this Person to register the Cloud Gateway server in EmpowerID. During the registration process, EmpowerID verifies the Person has the appropriate access and then generates a certificate and stores it on the server with the Cloud Gateway Client. The public key is sent to EmpowerID and mapped to the EmpowerID Person used during the registration process. All subsequent calls to EmpowerID by the Cloud Gateway Client occur using certificate-based authentication. When the Cloud Gateway Client starts, it calls EmpowerID to retrieve information needed by it to connect to Azure. EmpowerID uses this same information to connect to Azure, constituting a point-to-point connection between EmpowerID in the Cloud and the on-premised Cloud Gateway Client.
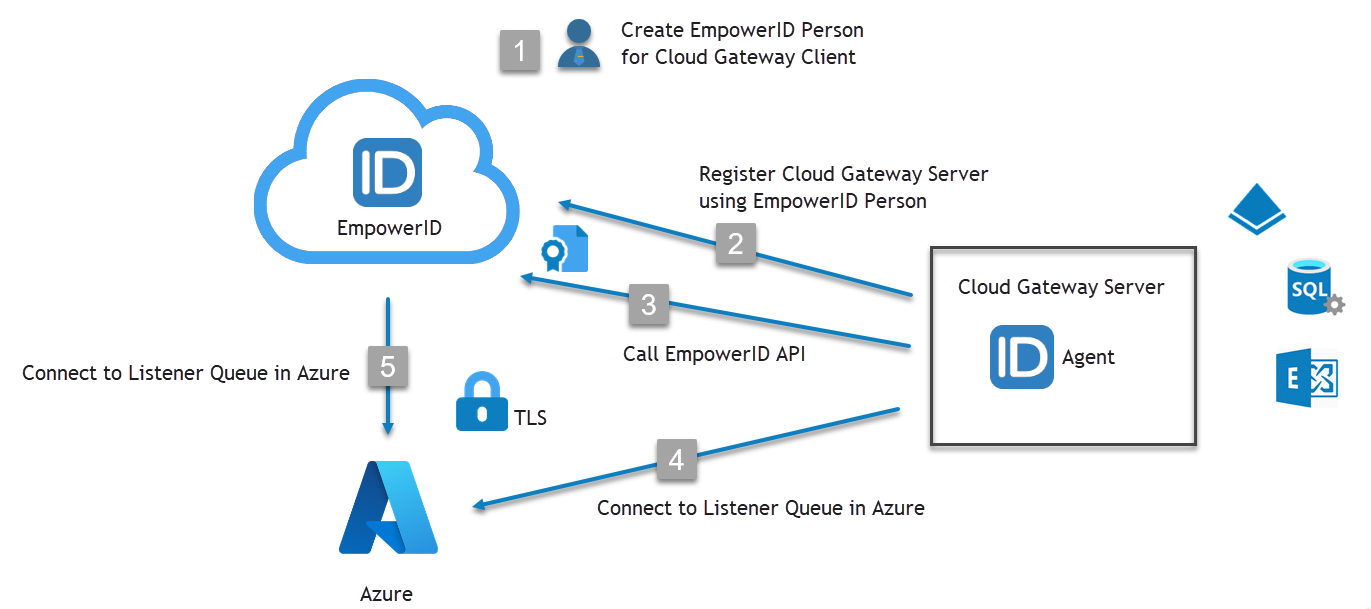
The above image provides a high-level overview of the process and communication flow that occurs between EmpowerID, the Cloud Gateway Client, and Azure. The process is as follows:
-
Step 1 – You create a dedicated Person account and assign to that Person the UI-Admin-Cloud-Gateway Management Role. The role gives the Person access to register and ping a Cloud Gateway server. This Person account should be solely dedicated for this use and should not be linked to an actual Person that uses EmpowerID for their daily activities.
-
Step 2 – You register the Cloud Gateway Client on a server using the EmpowerID Person account created above. If the Person successfully authenticates and has the required access, EmpowerID registers the client on the server, generates a certificate, and stores that certificate on the server hosting the Cloud Gateway Client. The public key is sent securely to EmpowerID as part of the registration process, where it is mapped to the Person account used to register the client. The certificate is then used to authenticate all communications between the client and EmpowerID.
-
Step 3 – The client securely calls EmpowerID to retrieve information needed by the client to connect to Azure.
-
Step 4 – The client connects to the hybrid queue in Azure using the information received from EmpowerID.
-
Step 5 – EmpowerID connects to the Azure queue using the same connection information sent to the Cloud Gateway Client, constituting a point-to-point connection between EmpowerID in the cloud and the on-premise Cloud Gateway Client. All such communications are secured via TLS.
Summary
The connector topology in Empower ID is designed to provide robust, flexible, and comprehensive integration capabilities. The array of connector types—from stock and universal connectors to custom and SKIM microservice framework connectors—enables organizations to configure and streamline their identity management processes effectively. By allowing seamless interactions between Empower ID and external systems, these connectors play a crucial role in the platform’s ability to support diverse environments and facilitate effective governance of identities and access across the organization. Understanding this connector topology is essential for leveraging Empower ID's full potential in identity management.
System Integration Architecture
Protected Resources and Resource Table
At the core of EmpowerID's functionality lies the concept of protected resources. These are the objects that EmpowerID manages, encompassing a wide range of entities from user accounts to groups, roles, and even workflow components. Every object in EmpowerID is represented as a resource in the resource table, which serves as a central registry for all managed items.
The resource table contains essential information about each resource, including its type, the resource system it belongs to, and basic identifying details. However, this is just the starting point. To provide a more comprehensive representation of each resource, EmpowerID employs a system of component tables. These tables, such as the account table, group table, or management role table, contain more detailed, type-specific information about each resource. For example, an account will have a basic record in the resource table, but its full set of attributes and specific account-related information will be stored in the account table.
Resource Systems
Resource systems are a crucial concept in EmpowerID, referring to the external IT systems that EmpowerID connects to and integrates with. Each resource system has its own record in the resource_systems table, complete with a unique identifier. The type of resource system is linked to the definition of the connector used for inventorying data from that external system. Interestingly, EmpowerID itself is considered a resource system, containing its own set of protected resources such as workflows, pages, roles, and APIs.
EmpowerID is capable of managing an impressive 73 different types of resources, ranging from Person and Account objects to more specialized types like Azure Application objects or SharePoint Online groups. This versatility allows EmpowerID to provide comprehensive management across a wide array of IT systems and object types.
Account Stores
A special category of resource systems is the account store. These are resource systems that contain identities which can be used for authentication, authorization, and other identity-related processes. Account stores extend the basic resource system definition to include detailed information about the identities they contain, their behavior, and associated authentication mechanisms. It's worth noting that not all resource systems have associated account stores. For instance, Exchange doesn't have its own account store but instead relies on identities from Active Directory or Azure AD.
Security Boundaries and Account Store Identity Entry
The concept of security boundary types is integral to understanding how EmpowerID interacts with different systems. A security boundary type defines the connector to be used when working with objects in an account store, as well as establishing relationships between account stores associated with the same security boundary. This becomes particularly important when dealing with complex systems like Active Directory, where multiple domains (each represented as an account store) might exist within a single forest (represented as a security boundary).
To manage the intricacies of different account stores and object types, EmpowerID uses the Account Store Identity Entry (ASIE). This implements the Create, Read, Update, and Delete (CRUD) methods for objects in an account store, along with defining the attributes specific to a particular security boundary type and object type.
Relationships and EmpowerID's Role
The relationships between these concepts can be complex but understanding them is key to effectively using EmpowerID. Resource systems can contain multiple account stores, and security boundaries group related account stores. This grouping allows for interrelationships between account stores within the same security boundary. For example, in an Active Directory environment, accounts from one domain can be members of groups in another domain within the same forest.
EmpowerID itself plays a dual role in this system, acting as both a resource system and a security boundary. It has its own account store definition for managing Person objects and Core identities within the EmpowerID system.
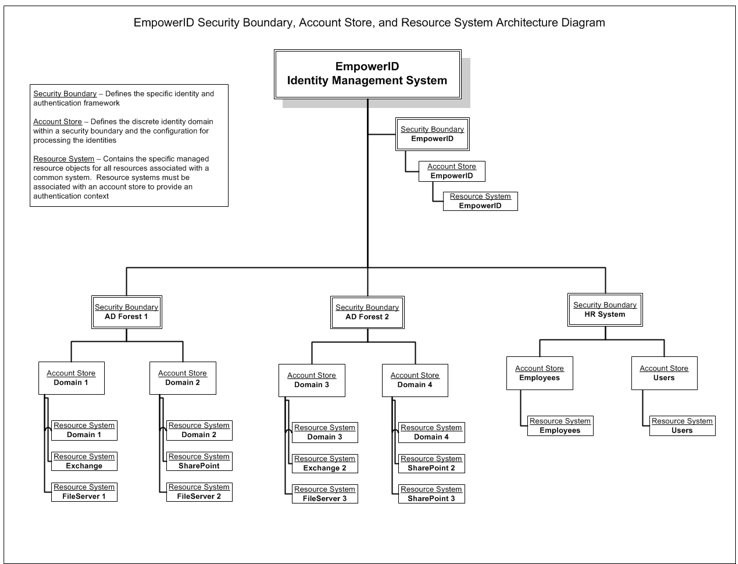
Conclusion
Understanding these concepts of resources, resource systems, account stores, and security boundaries is crucial for effective identity and access management within EmpowerID. They form the foundation upon which EmpowerID's powerful management and governance capabilities are built, allowing for comprehensive control and oversight of complex IT environments.
Applications in Empower ID
Application objects in Empower ID represent external operational programs that utilize identity resources managed by the platform. They serve to bridge user authentication and access management with the various account stores and resource systems within the organization. Understanding how applications interact with these elements is essential for effective identity and access management.
Key Aspects of Applications in Empower ID
Relationship Between Applications and Account Stores
-
One-to-One Relationship: Typically, each application has a corresponding account store that represents its internal directory. This account store holds the identities and access rights needed for that specific application to function.
-
Shared Account Stores: In some scenarios, multiple applications may share the same account store. When this occurs, administrators can specify which groups or roles within that store are relevant for each application, allowing for tailored access and security configurations.
Tracking Only Account Stores
-
Empower ID supports the concept of "tracking only" account stores. These account stores represent external systems or applications that may not have direct integration with Empower ID.
-
Purpose of Tracking Only Account Stores: These stores allow organizations to maintain a logical representation of identities that reside outside of Empower ID. While these identities may not be directly managed (in terms of automated provisioning, etc.), Empower ID can still track and manage them for reporting, auditing, and request fulfillment purposes.
-
Manual Processes: When actions need to be taken on tracking only account stores (such as user provisioning requests), Empower ID can issue manual fulfillment tasks. This process might involve sending requests to system administrators or owners to create or update corresponding records in the external application.
Applications Configured for Single Sign-On (SSO)
-
For applications that require SSO, it is essential to create an application object within Empower ID. This object serves as the configuration point for establishing federated connections between Empower ID and the external system.
-
Benefits of SSO Integration: SSO reduces the number of credentials users need to manage, enhancing user convenience and security by minimizing password-related risks. It streamlines the user experience and ensures that access controls are consistently applied.
Application Objects in Empower ID
-
Each application is defined by an application object that stores essential details about the application, including:
- Name: The name of the application.
- Type: The type of application (web, mobile, etc.).
- Endpoints: The relevant URLs or endpoints needed for integration and authentication.
- Linked Account Stores: The account stores that provide identities for authentication and authorization.
-
Configuration Options: Administrators can set various configurations for each application object, including specifying the authentication methods used, defining roles, rights, and permissions within the application.
Summary
Applications within Empower ID play a crucial role in linking user identities to operational capabilities while providing a structured mechanism for managing access rights. With their association to account stores and the provision for tracking only account stores, applications ensure that organizations can maintain robust identity management practices across their ecosystems. By leveraging Empower ID's capabilities for SSO and application lifecycle management, organizations can enhance security, user experience, and efficiency in their identity and access management strategies. Understanding the intricacies of application management in Empower ID is vital for optimizing how organizations manage identities within their operational frameworks.